The password manager is not an ordeal!
We've seen that a password must :
- Be longer than 12 characters.
- Contain characters chosen from 90.
- Be randomly generated.
- Not be “guessable”.
In other words, if you're able to remember just one of these passwords, it's because it doesn't meet all these criteria (or else you're potentially affected by a personality disorder...).
A practical and reliable tool has been designed for just this purpose: the password manager. The aim of this section is not to compare existing products, but to show you how the 2 below work:
- If you're fully equipped with Apple, the iCloud Keychain does the job very well, and there's nothing better in terms of ease of use.
- If you have even a single Android/Microsoft device, or would like to use an open source solution, then you'll need to turn to a third party, and Bitwarden will do the job perfectly, with ergonomics very similar to iCloud.
Once downloaded, the choice of password manager to use is set in => Settings/General/AutoFill & Passwords: !
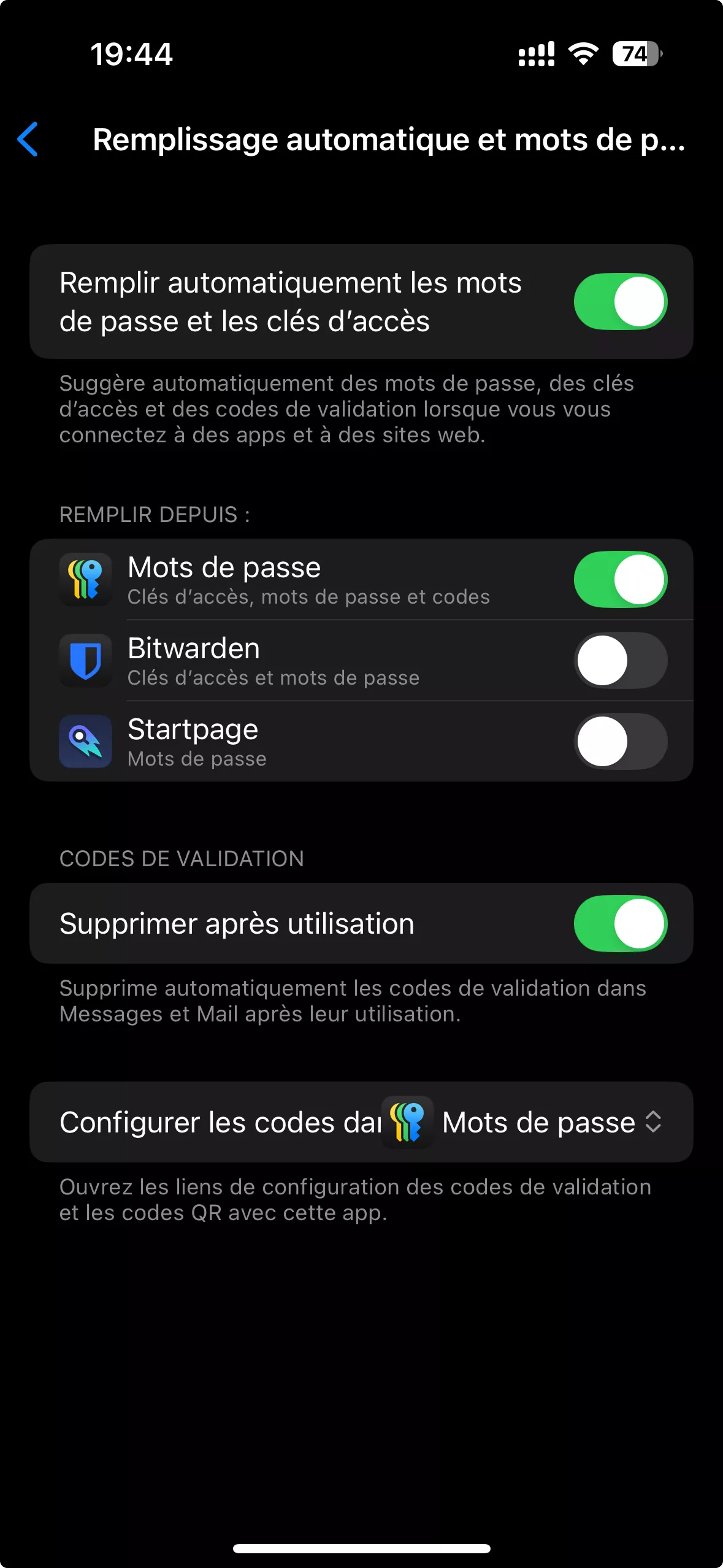
Native manager: iCloud Keychain.
By default, iOS (and of course macOS) implements its Keychain to manage all information (such as Safari and app usernames, passwords, identification keys, credit card information and security codes, Wi-Fi passwords) as transparently as possible. All you need to do is create an iCloud account and set it up => Settings/iCloud/Passwords and iCloud Keychain/Synchronize this iPhone. This setting allows Keychain information to be synchronized with all Apple devices connected with the same iCloud ID in a secure manner (E2EE).
Advantages :
- End-to-end encryption.
- Storage and use of Passkeys since the end of 2022 (iOS 16).
- Synchronized with all other associated Apple devices.
Disadvantages:
- Only available on iOS.
- Access security dependent on terminal unlock code => beware of 4-digit PIN codes...

How it works:
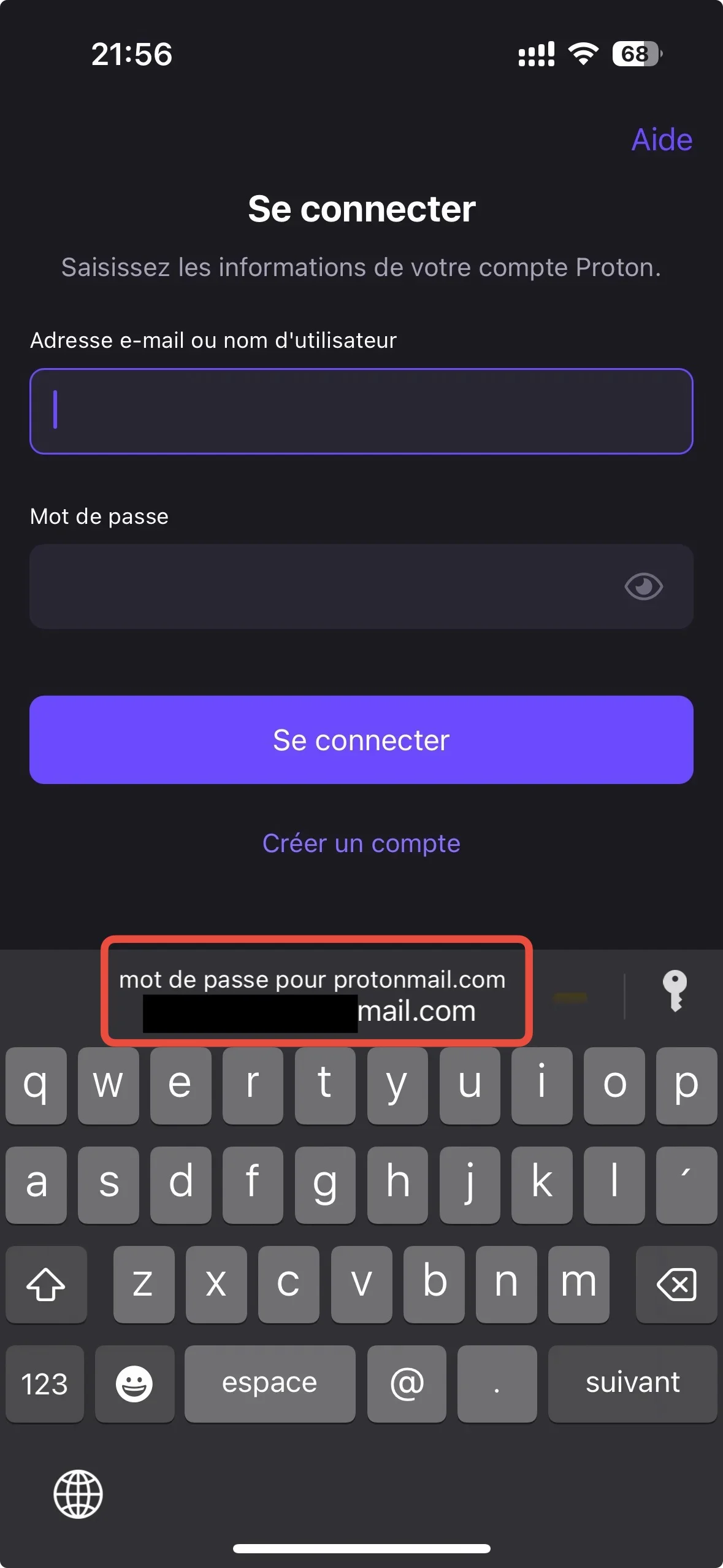
It could hardly be more transparent! A site's login window appears, asking for a login/password?
=> it offers you to fill it in automatically with your keychain information.
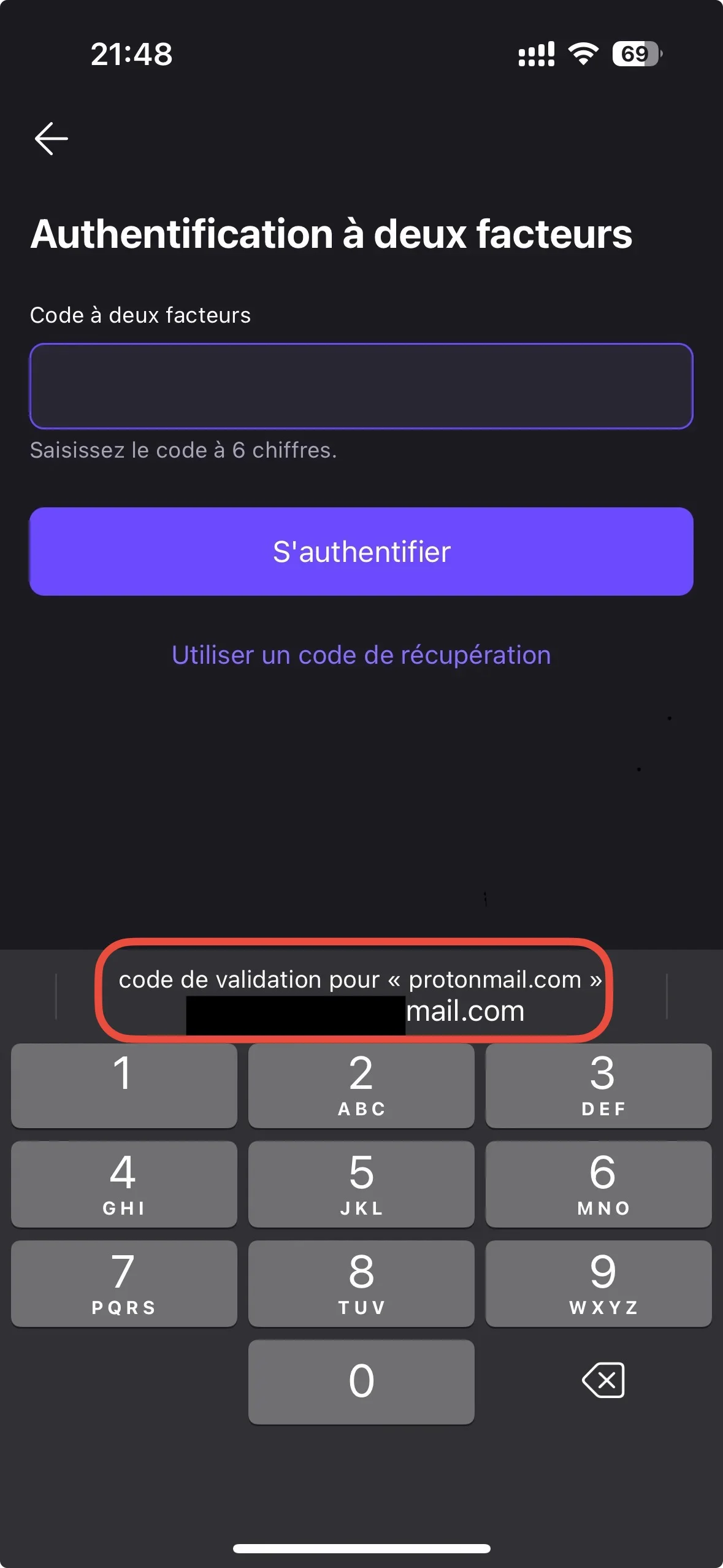
Is double authentication activated for this account?
=> Just click on "Validation code" to copy it automatically from the Passwords app.
Security : AES-256 algorithm used to encrypt data. Generated passwords contain 20 characters. They contain 1 number, 1 uppercase letter, 2 hyphens and 16 lowercase letters. Generated passwords are strong, with an entropy of 71 bits.
Passwords are audited and problem passwords are clearly identified as follows: Reused - Weak (dictionary passwords, keyboard sequences, character substitution) - Associated with a data leak.
Features : Automatic password filling when accessing an identification web page - Sending passwords via Airdrop (bluetooth encrypted with TLS)- Wi-Fi password sharing - Export possible via MacOs.
Third-party manager: Bitwarden.
If you go elsewhere, it's because you're looking for an ultra-compatible solution (when you've got dozens of passwords, you want to be able to use them anywhere) and because it's even more secure than the original. There are a multitude of applications claiming this on the market, some free, some paid, some based on proprietary code, some open source, some proven, some failed (LastPass in 2022)... Logically, the application that could have been chosen is Keepass, which is highly secure and recommended by ANSSI. It collects no personal data (whereas Bitwarden collects at least billing data). But the absence of a browser extension, a native mobile application and an arid interface that makes its use unintuitive left it on the bench.
Why Bitwarden? Open source guarantees the absence of backdoors, with audits and pentests carried out every year (Cure53), security (AES 256 encryption algorithm and PBKDF2 hash algorithm by default and Argon2i configurable - E2EE and zero-knowledge), confidentiality (GDPR compliance), ease of use (OS and browser integration - vault imports and exports possible), and contained price (free in the basic version for individuals and only $10/year for the full version integrating MFA).
It works in the same way as iCloud Keychain:
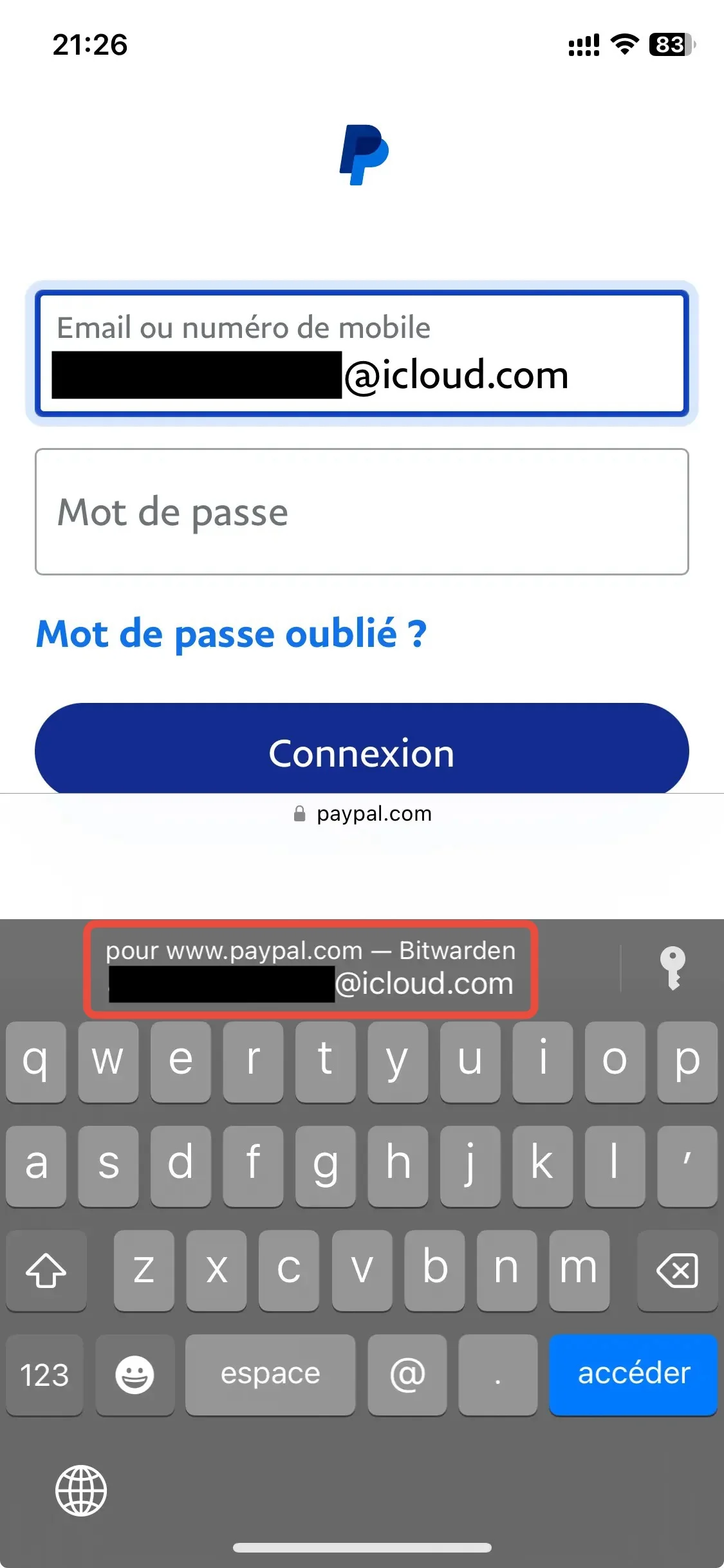
- Once you've installed the extension on your browser, it's as fluid as the native iPhone manager, and automatically fills in or creates passwords in the login windows that open.
- Admittedly, finding the difference with the way the iOS app works takes some attention! (Bitwarden on the left and iOS App on the right).

Advantages :
- Available for all platforms/browsers (including Tor).
- Enables you to require the use of a password (it's the only one you'll have to remember) and not just the terminal unlock code.
- Choose the strength of the password or passphrase to be generated.
- Protect account access with MFA or Passkey.
- Storage and use of Passkeys (since mid-2024 on iOS).
- Synchronization on cloud (choice of Europe/USA server) or self-hosted.
- Its paid version also offers storage (up to 1 GB), encrypted file upload (max. 100 MB) and password security reports.
Disadvantages :
- 2FA management by TOTP codes only available in the paid version.
- Password sharing would gain in fluidity by being available from the vault rather than copy/paste into Send.
The future: the end of passwords and the widespread use of Passkeys.
We've just seen that the most robust multifactor authentication comes from the protocol produced by the FIDO alliance (FIDO U2F). This is not, however, the most recent version proposed by this industry association of major digital players. Its mission? To promote authentication standards that “contribute to reducing the world's excessive dependence on passwords”. At least that's clear! The latest version, called FIDO2, is made up of Web Authentication (WebAuthn) and Client to Authenticator Protocol (CTAP2), and enables password-free authentication directly on a site in the most secure way possible. In simple terms, WebAuthn requires the browser to mediate authentication, while CTAP2 handles communications between the two.
CTAP2. This is a cryptographic authentication-based protocol, derived from U2F, which manages the connection between the authenticator (a FIDO2 key or terminal) and the user.
WebAuthn. This is an authentication protocol that uses asymmetrical cryptography within a browser. Supported browsers are Brave, Chrome (versions 67 and later), Edge (versions 18 and later), Firefox (versions 60 and later), Opera (versions 54 and later), Safari (versions 13 and later). It manages the authentication part between the user and the website server.
The synthesis of these 2 protocols => PASSKEY. A cryptographic identification key (Passkey) is created upon enrolment on the website (public key sent to the site - private key secured on the user's terminal or hardware token).
1 - When connecting to a site, the user uses his private key (securely stored on the terminal or a hardware key such as Yubikey) to identify himself to the server. 2 - The server identifies the user requesting connection and sends back a “challenge” encrypted with the user's public key.
3 - The user's terminal then solves the challenge using its private key, and transmits the result to the site's server, which authorizes access.
Passkey use is just as seamless with the Bitwarden app (left) as it is with Passwords (right). Best of all, once you've configured Face ID access, Passkey use is secure and invisible, while connection is instantaneous and requires no further manipulation of the iPhone =>
With Passkey, passwords are a thing of the past!


Advantages
- Interoperable on all terminals in the same ecosystem, thanks to cloud synchro (iCloud Keychain).
- Interoperable on terminals from different ecosystems using password managers (Bitwarden) or hardware tokens (Yubikey).
- Authentication is impervious to man-in-the-middle attacks, phishing or data leakage.
- Preserves anonymity since no identifier is required (only an exchange of anonymous cryptographic keys).
- Meets the MFA definition: the Passkey is the possession factor, the implementation of biometrics or a PIN to unlock the terminal is the knowledge factor.
Disadvantages
- Few sites offer this technology (around 200 listed on "passkeys directory").
- It is not interoperable between terminals from different ecosystems, unless third-party applications are used.
- If you delete your account on a site, this only deletes the public key present on the site (you'll have to delete the corresponding private key on your side).
- It depends on the security of the hardware token, which may be lost/stolen, the browser, which may be compromised by malware or a security flaw, the terminal, which may be infected...
- A team of researchers has audited the standard and criticized the choice of the elliptic curve used in the ECDAA cryptographic system on which the FIDO Alliance is based.
Summary :
| Support | Security | Compatibility | Ease of use | Economy | Total points |
|---|---|---|---|---|---|
| iCloud Keychain | [3] | [3] | [1] | [1] | [8] |
| Bitwarden | [2] | [2] | [2] | [2] | [8] |
| Yubikey | [1] | [1] | [3] | [3] | [8] |
The 3 supports come out surprisingly equal, which shows that you'll have to select according to the most important criterion in your eyes, but here are a few things to think about:
- All 3 are secure (E2EE) and have not failed to date (at least officially).
- The security of a software solution present on the same terminal as the one used for the connection will always be weaker than that of a hardware solution.
- Is the risk of losing hardware support and the ensuing hassle worth the investment and the loss of “fluidity” generated by handling a hardware accessory?
What about you: What means are you going to use to ensure your safety?
